¶ Overview
Inseego 5G SD EDGE ZTNA Broker (Zero Trust Network Access) appliance is a virtual machine that integrates with EDGE Manager and enables Wi-Fi AAA capabilities.
Network AAA refers to three services used to control connectivity and increase security:
Authentication: Identifies the user (or laptop in the case of machine-based credentials) by username/password combination or a certificate private/public key pair.
ZTNA-B supports authentication modes:
· Local authentication
· External RADIUS
· Azure AD
Authorization: Determines what the user is allowed to access or do.
Accounting: Provides information on what the user is doing, such as logging or data usage.
¶ ZTNA components
ZTNA solution consists of the following components:
· ZTNA Broker
· EDGE Manager
· CPE (which devices connect to via Wi-Fi)
· External RADIUS server or Azure AD (optional)
¶ Planning
| Value | Default | Notes | |
| ZTNA Hostname | |||
| ZTNA LAN IP* | (dhcp) | Placing ZTNA Broker in the same subnet as either EDGE Manager or CPE is not currently supported. | |
| ZTNA WAN IP* | |||
| EDGE Manager URL* | |||
| EDGE Manager Admin credentials* |
*Required
¶ Setting up ZTNA Broker
Follow these steps in the order provided to set up your ZTNA Broker.
¶ Step one: obtain an Open Virtual Appliance (OVA)
Contact your Inseego Sales representative to obtain an OVA.
¶ Step two: deploy the OVA
Refer to the VM deployment guide. Insert link.
¶ Step three: configure port forwarding and any necessary firewall rules
Use the port forwarding/firewall reference to configure port forwarding to ZTNA Broker and set any necessary firewall rules on the enterprise network that is servicing ZTNA Broker. Contact your network administrator for assistance.
Port forwarding/firewall reference
| Notes | |
| Source | 0.0.0.0/0 |
| Destination | WAN IP of ZTNA Broker |
| Ports/protocols | 1443 |
| NAT rule | Destination NAT to LAN IP of ZTNA Broker |
| Source | LAN IP of ZTNA Broker |
| Destination | 0.0.0.0/0 |
| Ports/protocols | Any |
| NAT rule | Source NAT to WAN IP of ZTNA Broker |
¶ Step four: onboard ZTNA Broker to EDGE Manager
· Login to the ZTNA Broker server through the VM console, serial console, or SSH using the following credentials:
Username: root
Password: oelinux123
NOTE: The root credentials are overwritten during onboarding and retrievable from EDGE Manager.
· Run the command to onboard the device:
Command : bash /opt/inseego/bin/ztpcurl.sh <proto> <url>:<port>
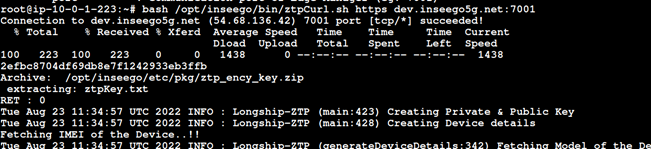
· Once the device appears in the Onboarding Devices page of EDGE Manager, select it and click Approve.
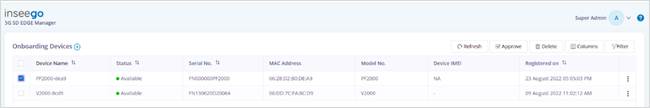
· After approval ZTNA Broker moves to the Devices page.
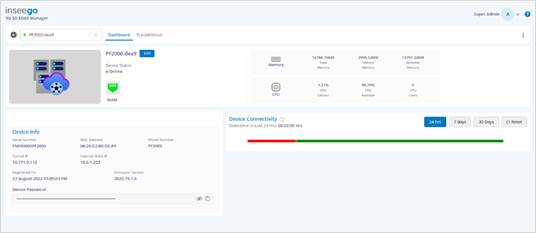
¶ Step five: configure ZTNA Broker in EDGE Manager
· Open the public URL of ZTNA Broker: https://x.x.x:1443/.
For example:
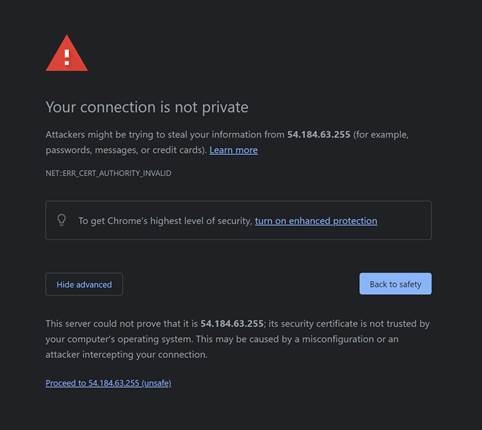
Click on Advanced Option and then Proceed to x.x.x.x (unsafe).
Go to EDGE Manager.
NOTE: The certificate warning is due to the default, untrusted certificate. The certificate can be replaced later with one signed by a trusted Certificate Authority.
· Once ZTNA Broker is online in EDGE Manager, navigate to Configuration > Packetfence. The interface details are auto populated.
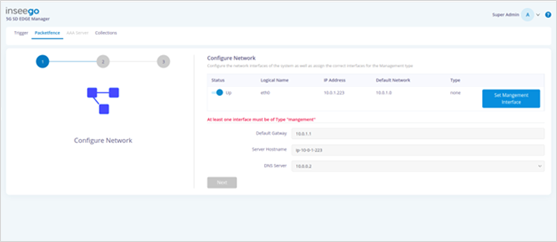
· Click Set Management Interface and then click Next.This marks the interface as management. Step 2 of the Configure Network wizard appears.
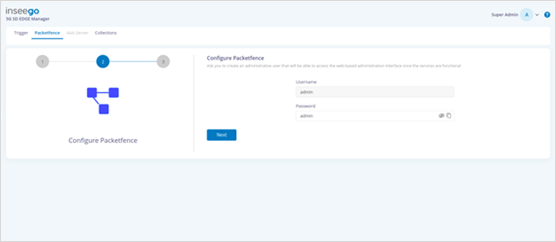
Alternatively, click the Set Management Interface button on the public URL of ZTNA Broker: https://x.x.x:1443/.
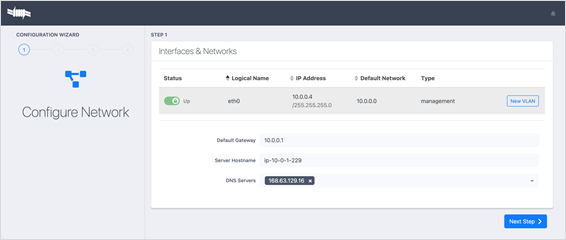
· Update the admin password and click Next. Step 3 of the Configure Network wizard appears.
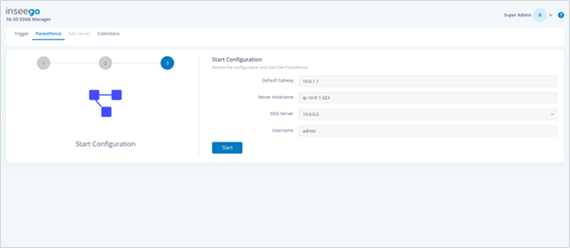
· Verify the start configuration information and click Start.
· Open the AAA Server tab.
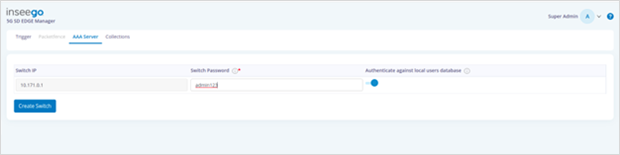
· Update the switch password and click Create Switch.
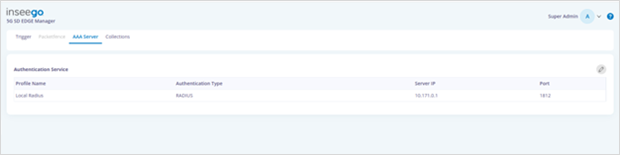
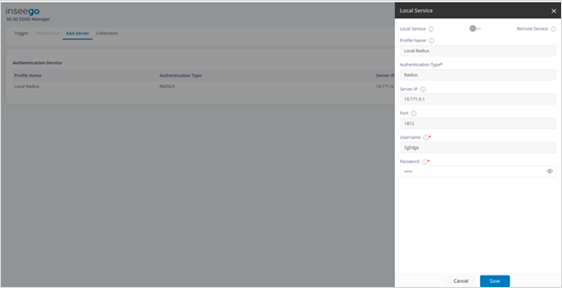
· Select the service and update as follows:
For Local Service: Update Password
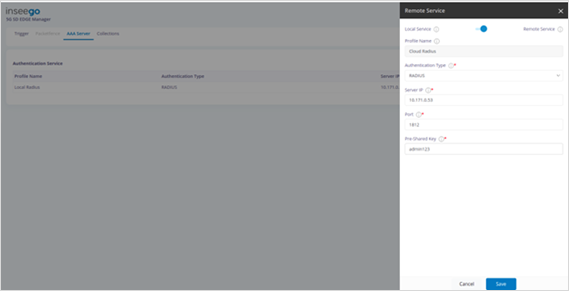
For Remote Service: Update Server IP, Port, and Pre-Shared Key
¶ Step six: use a local, external RADIUS or Azure AD account
You can use a local account, an external RADIUS account, or an Azure AD account for initial testing.
¶ Use local (default)
One local user is created by default for testing.
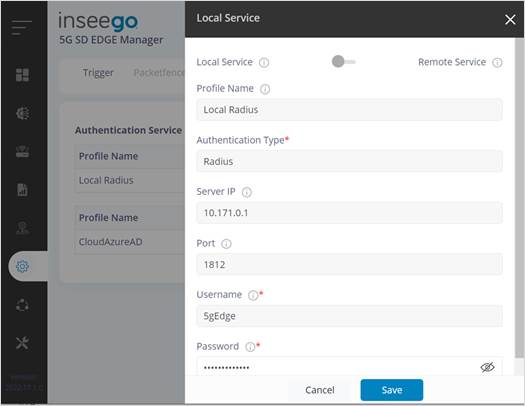
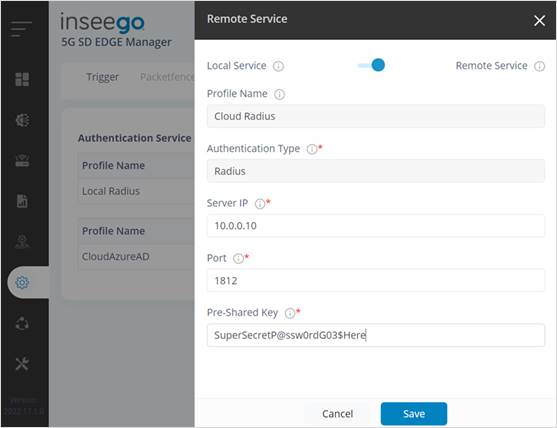
¶ Use external RADIUS (optional)
· From EDGE Manager Configuration > AAA Server, select the service and move the slider at the top from Local Service to Remote Service.
¶ Use Azure AD (optional)
To use Azure AD, you must have an AD user account and an application registered in the same Directory.
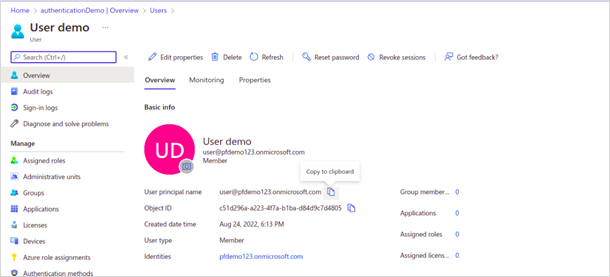
¶ Create a user in the Azure portal
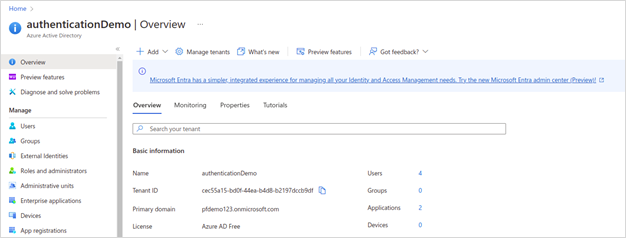
If you already have a registered user in the same Active Directory then you can proceed using the same user credentials, otherwise, follow these steps to create a new user:
· Login to the Azure portal: https://portal.azure.com/signin/index/.
· Search and move to Active Directory service.
· In the Add dropdown, select User.
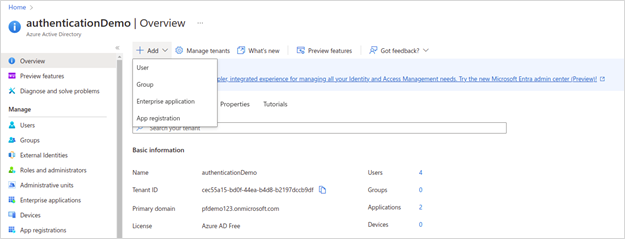
The New user page appears.
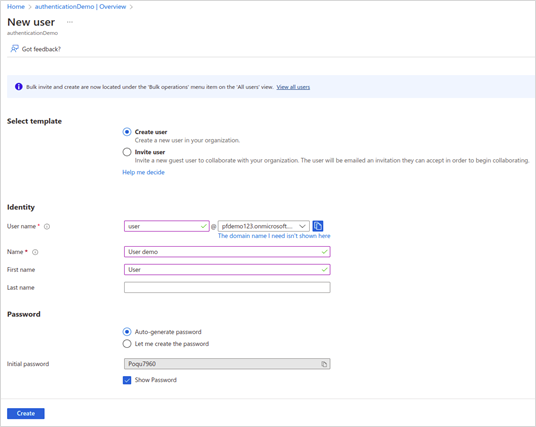
· Fill in the information and click Create. An overview appears.
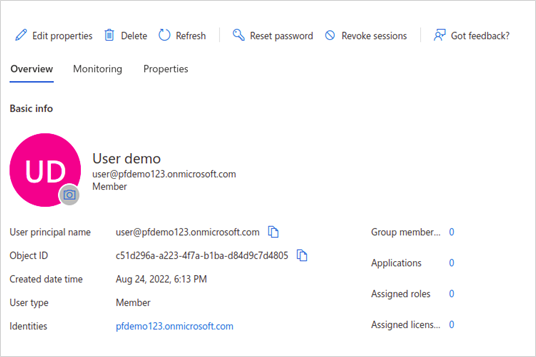
· Copy and store the User principal name for future use.
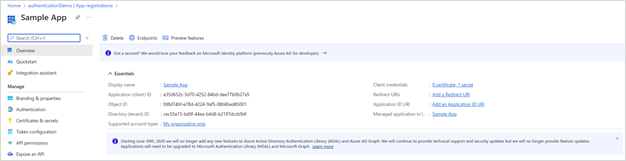
· In the Add dropdown, select App Registration. The Register an application page appears.
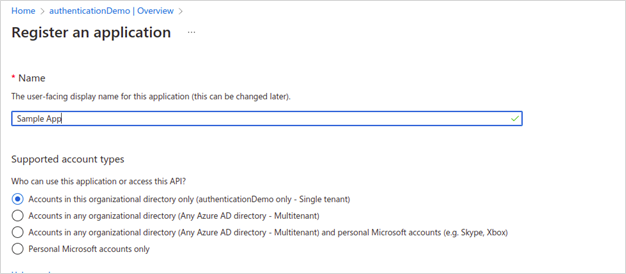
· Register the application.
· Select Manage > Certificates & secrets to create a client credential and select a new client secret.
· Copy and store the Client Secret ID for future use.
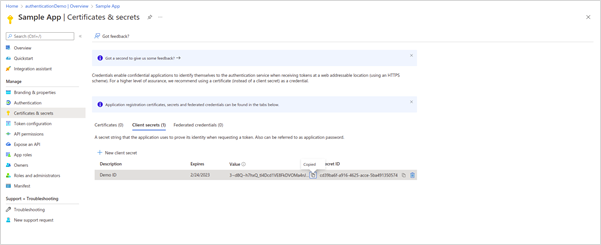
· Select Manage > API permissions, then select Add a permission and Microsoft APIs > Microsoft Graph.
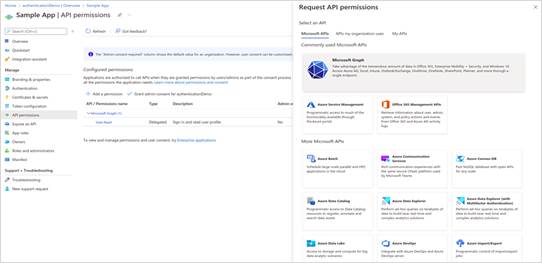
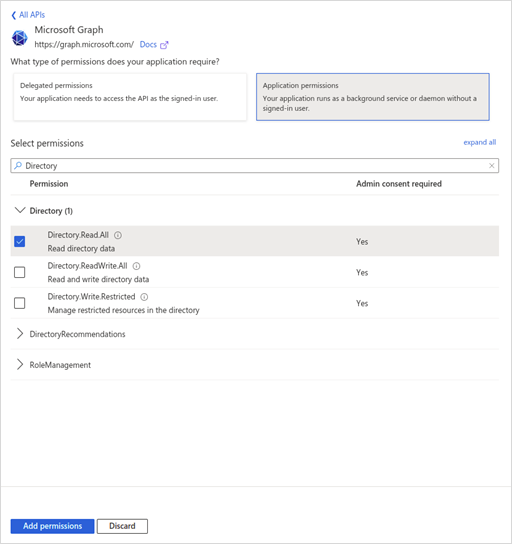
· Select Application permissions, check the Directory.Read.All box and click Add permissions.
· Copy and store the Tenant ID for future use.
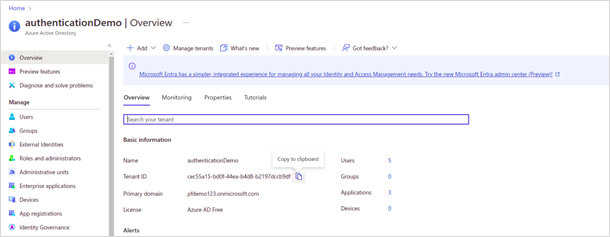
· Copy and store the User principal name for future use.
¶ Configure the Azure AD profile in EDGE Manager
· In EDGE Manager, navigate to Configuration > AAA Server.
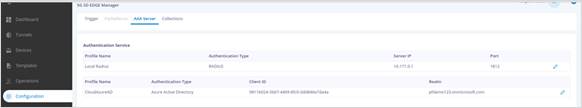
· Select the Azure AD profile.
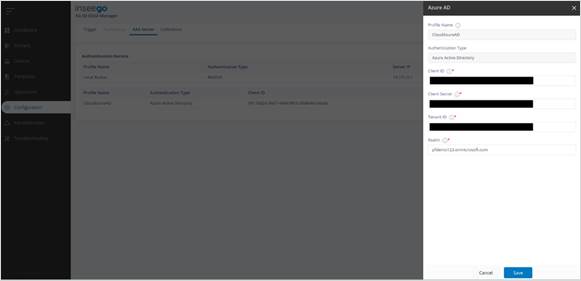
· Configure the Client ID, Client Secret, Tenant ID, and Realm.
Example:
Profile Name: Can be configured as CloudAzureAD
Client ID: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Client Secret:
Tenant ID: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Realm: mycompany.onmicrosoft.com
NOTE: WPA3 and 802.1X authentication of users using Azure AD only works with supplicants configured to perform EAP-TTLS PAP, which provides the RADIUS server with the plain-text password of the user.
¶ Step seven: create a Wi-Fi template with an enterprise SSID
· In EDGE Manager navigate to the Templates page and click on the plus sign

next to Templates to add a new template.

The New Template dialog appears.
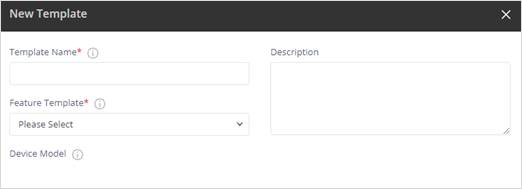
· Enter a template name and select Wi-Fi Configuration from the Feature Template dropdown.
· Select SSID and click on the plus sign next to Settings. The Add New SSID dialog appears.
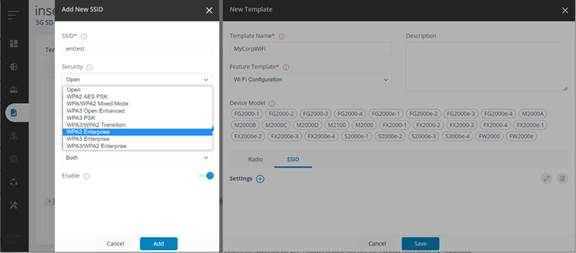
· Enter a name for the SSID and select an enterprise security from the Security dropdown (WPA2, WPA3, or WPA3/WPA2 per your organization's policies). Click Add and then Save.
¶ Step eight: verify SSID functionality
NOTE: For client configuration, you can use a Mobile Device Management (MDM) or Group Policy solution to push settings to multiple users or devices via policies, eliminating the need for manual configuration.
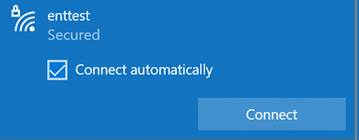
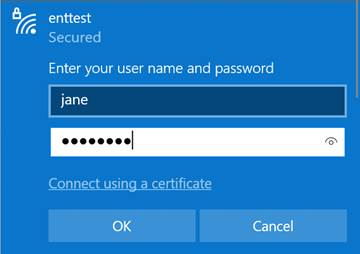
¶ Configure a Windows client with local authentication (example)
· Connect with your test user to verify SSID functionality.
¶ Configure a mobile client with Azure AD authentication (example)
· Connect to the SSID.
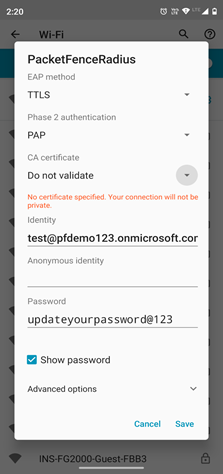
· Configure PacketFenceRadius as follows:
EAP method: TTLS
Phase 2 authentication: PAP
Identity: xxxxxxxxxx
Password: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
· Click Save.
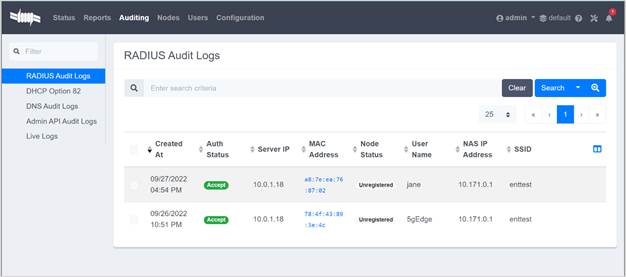
¶ Step nine: review audit logs (optional)
· Review the RADIUS audit logs on the ZTNA Broker.
¶ Step ten: add local users on ZTNA Broker (optional)
· Navigate to https://WANIPofZTNA_Broker:1443/.
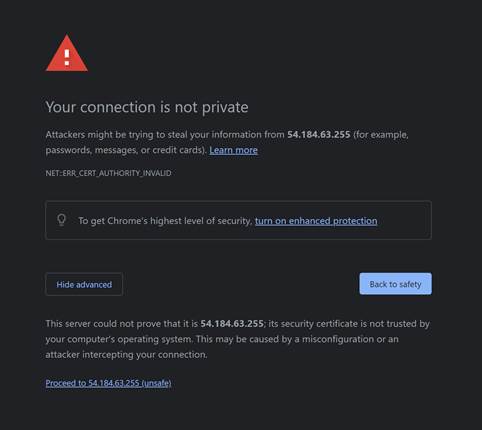
· Click on Advanced and then Proceed to x.x.x.x (unsafe). NOTE: You can install a trusted certificate.
· Login with the admin credentials provided during setup.
· Navigate to Users.
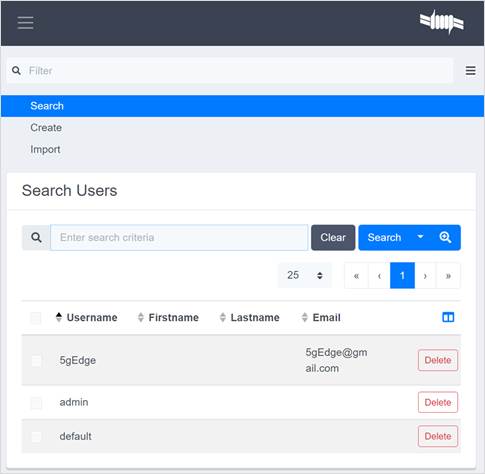
· Select Create and then choose the Single or Multiple tab.
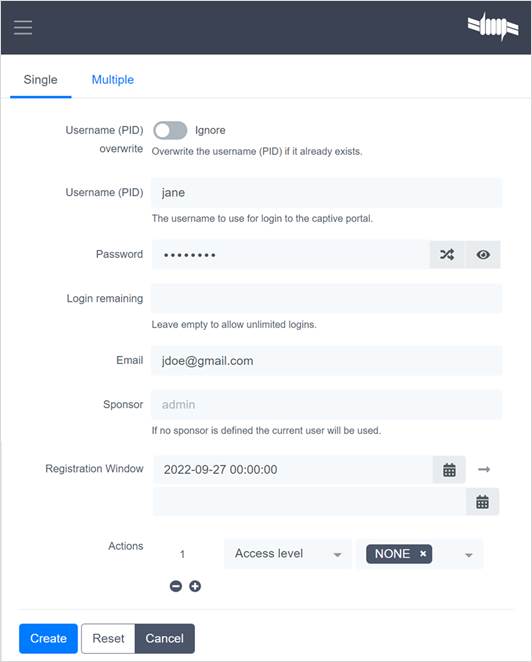
· Define the user(s) and click Create.